Inkjet & Digital Printing
Ricoh Information Security and Document Security
Friday 04. July 2008 - When connecting digital devices to your network, there should be assurance that system resources and data are protected from disruptive forces inside and outside your organization. This enables IT management to embrace products that would otherwise pose a security risk, while providing employees with high-performance equipment that streamlines workflow, protects vital business interests, and ensures peace of mind.
The Framework Concept
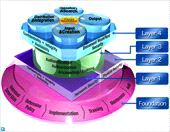
The Document Security Framework concept (see Figure 1) is derived from Ricohs extensive research into our customers document-related business processes, as well as respect for the considerable IT investments that have been made. Central to this framework is Ricohs commitment at each Layer, starting with the Physical Security and Network Security Layer (Layers 1 & 2).
These Physical Security and Network Security countermeasures are just a few basic methods used to maintain document and data Confidentiality, Integrity, and Availability.
Once the basic security measures are implemented, stages in the document workflow must be protected as well. This includes input & creation, output, repository & search, distribution & integration (Layer 4). Layer 4s foundation is comprised of Authentication, Authorization and Accounting/Auditing countermeasures (Layer 3). The AAA Security Layer safeguards the document workflow.
Once the AAA Security Layer is implemented, the document workflow can include correct and safe processes governing information input & creation, output, repository & search, distribution & integration. It will then be possible to establish proper Document Workflow Security (Layer 4). This can include MFP integration with backend Document Management Systems (DMS) that provide organizations with the power to control information assets, and meet stringent compliance requirements.
After deploying countermeasures, processes should be reviewed according to the Demings Plan – Do – Check – Act (PDCA) cycle. For example, in the planning stage, its important to understand the current state of security and define any new policies. To ensure proper use and maintenance of countermeasures, employees must also understand the policies.
Furthermore, auditing should be conducted from time to time, in order to check if the security procedures are successful, or if modifications are necessary (Foundation).
Ricohs Common Sense Approach
to Information Security
Keeping the Document Security Framework in mind, Ricoh believes you should take a multi-layered approach to security, one that combines two key objectives: streamlined, efficient workflow, and document security. The goal is to create a controlled system that minimizes risks to information security without unduly impacting document administrators, users or workflow processes.
If the security measures are too costly or complex to roll out, the controls may negatively impact productivity; users may resist.
So, after identifying vulnerabilities and threats to information security, we recommend that you consider solutions that:
Do not overreact to the perceived risk Are non-intrusive
Are affordable Require little or no training
